A good eCommerce business requires good security. Security for eCommerce is of pivotal importance in the 21st century. Why is that?
According to the latest data, 70% of small businesses are completely unprepared for a cyberattack. Also, the prediction shows that more than 33 billion online accounts will be hacked in 2023 alone.
That’s not all, more than 80% of hackers can get through the defenses of an online business in around 12 hours!
These are alarming facts for any online entity, especially if it is a WooCommerce store.
Our discussion today addresses this issue. Together, we will explore eCommerce security, what it is, what are the notable issues, and what are the proven ways to solve it?
Security for eCommerce [What You Should Know]
eCommerce security is nothing more than a set of guidelines that highlights a set of dimensions for optimal performance while maintaining security. For example, you have a set of security rules to save your physical store from theft. The concept is similar.
eCommerce security solutions have some security dimensions.
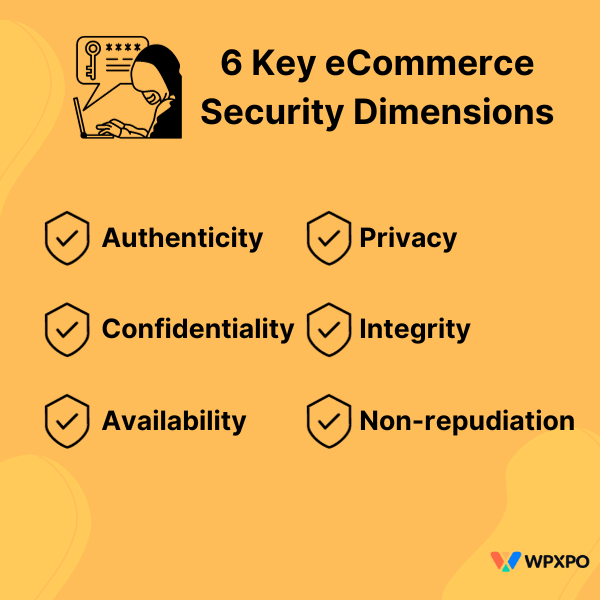
6 Key eCommerce Security Dimensions
There are 6 key dimensions to the eCommerce security aspect:
Authenticity:
In terms of security for an eCommerce website, authenticity refers to the real identities of the seller and the buyer.
Unfortunately, the authenticity dimension isn’t easy to control. Unwanted 3rd parties can use fake email addresses and compromise authenticity. Although there are safeguards in place, authenticity control between the buyer and the seller can be difficult.
Confidentiality:
Confidentiality is easy enough to understand. It deals with the fact that the user identity and the merchant identity remain intact and no one can steal the data. This way, the data confidentiality remains intact.
There is a chance of 140+ billion data breaches between the years 2018 to 2023. The real number is estimated to be more because of the introduction of AI tools.
Packet sniffing tools can breach data confidentiality. Using these tools, hackers can easily steal the customer purchase history, and other forms of data.
Availability:
An eCommerce store needs to be available 24/7. A buyer can come at any time to make a purchase. If the data availability is not regular, the site owner will lose a competitive advantage.
That’s what availability stands for!
If a customer cannot make a purchase from a WooCommerce store, the availability aspect is no longer valid. It means the site integrity is not complete.
Privacy:
Data privacy refers to the control over an individual’s data provided by the merchant or admin.
For example, if you are a registered buyer at an online wholesale store, the site admin is bound to give you full access to the users data. You can change the information or choose not to provide any confidential information.
Also, the site owner is liable to provide adequate facilities to tackle eCommerce security threats.
Once a hacker gets access to an eCommerce website, data privacy is broken. Once such a breach occurs, it may cause catastrophic damages to the user(s) who have been exposed to such attacks.
Integrity:
Integrity of data is when the information from the customer reaches ‘without change’ to the online merchant.
For example, if a user sends his or her credit card details through the online eCommerce portal and the data reaches unaltered without interception – the integrity of the data is safe. Hence, eCommerce website security remains intact.
However, data integrity is compromised if an unwanted 3rd party intercepts the data in transit and changes the information.
For example, let’s say you were making a $200 purchase from an online clothing store. If the unwanted entity somehow managed to get ahold of the data before it reached the site admin/merchant changed the price to $350 and added some items to the cart, the merchant or the customer would not be able to catch the changes in time.
Non-repudiation:
It means the transaction is valid and will not be denied by any entity.
For example, there are certain things you need to do to order a product from an online WooCommerce store. If a customer doesn’t follow all the steps, there is a chance the customer may not receive the product. Non-repudiation ensures the customer agrees to receive the product once he or she places an order.
Otherwise, the merchant or shop admin hold the right to deny the request.
9 Known eCommerce Security Threats [Threats to Know About]
The types of security threats are many. However, there are a number of security threats that have a higher chance of occurrence. We will be talking about them in the coming sections.

1. Brute Force Attacks
This is the simplest form of attack on an online website or server. The attacker tries various methods to try and guess a user’s email identification and password and use it to access the site of that particular user.
When an attacker successfully executes a brute force attack, he or she can gain access to the user’s data. It is one of the most used methods for identity theft and fraud.
Different types of brute force attacks
There are different types of brute force attacks. Some common types of attacks are:
- Simple Brute Force Attack: A manual form of attack that involves the hacker trying to guess the login credentials of a user. Weak password etiquette can lead to the success of such attacks.
- Reverse Brute Force Attack: If a hacker somehow recovers your old password, they will be able to use it to recover your latest password. These types of attacks are successful when you use repeat characters for your passwords. Attackers study the old password and try to guess the new login details.
- Credential Stuffing: Credential stuffing is similar to reverse brute force attack as it involves analyzing the password patterns of a user. Again, users who use similar login IDs and passwords for their sites.
There is another form of credential attack called the dictionary brute force attack – the chances of success of this type of attack are very low. Also, the hybrid attack uses both the simple and the dictionary attack to gain success (for the attacker of course!).
Using strong passwords is the only possible way to counter the brute force attacks. We will discuss password security in the coming sections.
2. Malware Attacks
Another eCommerce website security threat is attacks from malware or malicious software. There are different forms of malware attacks that can compromise WooCommerce security:
- Keyloggers: These are another form of malware that logs the keystrokes of a user. Hackers can easily fish the login data from the keylogger and gain access to sensitive data.
- Backdoors and Rootkits: Backdoors and rootkits are tools attackers use to gain “back-door” access to eCommerce websites. This access allows the attackers to gain sensitive information about the users registered to an eCommerce site.
These are some of the potential eCommerce security threats you can observe from malware attacks. However, there are other forms of malware attacks – you will see them in a bit.
The best way to be safe from such attacks is not to click on “flashy” or “fishy” online ads or websites. Other potential eCommerce security solutions against malware will be shared in the later sections.
3. Ransomware Attacks
Only in the US from June 2022 to July 2023, over 1400 ransomware attacks were recorded. The latest reports show no slow-downs in ransomware attacks.
It is a form of eCommerce security threat that locks all the files in your system. Then the attacker asks for payment to unlock all the files. Nowadays, hackers ask for Bitcoin as ransom to unlock the files in the system.
Ransomware can come in the form of malicious web links or downloadable files. As mentioned before, don’t click or download anything suspicious. It will help you be safe from ransomware attacks.
4. SQL Injection and Cross-site Scripting (XSS)
SQL injection is a critical web security vulnerability. Attackers use malicious code to manipulate the backend database of a website and view sensitive information like user access codes, general information, etc.
On the other hand, Cross-site scripting is another form of code injection where the hacker inserts malicious code into the website. The website is served to the user in the infected form. Unfortunately, there’s no way to learn that the site is affected. This can lead to identity theft online.
5. Trojan Horse
Trojan Horse is a type of malware that is still very prevalent in the eCommerce space. Also, more than 50% of attacks happen from trojan horses.
These are malicious programs in the cloak of useful software. In short, the system identifies them as useful programs, which they are not!
They remain mostly undetected by the user. During such time, the program helps the attacker gain all the important information about a user.
The use of a firewall is an ideal way to stop such programs from being installed on your system.
6. Malicious Bots
Malicious bots are often thought of as one of the main eCommerce security threats for the following reasons:
- These types of bots often try and gain unauthorized access to eCommerce websites
- They are used for software scalping where the product stock is depleted – raising the product prices
- These bots can scrape images from pages and create counterfeit online stores – leading customers to give their personal information
7. Man-in-the-Middle Attacks (MiM Attacks)
Man-in-the-middle attacks are common forms of cyber attacks. Hackers change the transaction credentials or purchase orders without the knowledge of the eCommerce site admin or the customer.
Attackers can deploy malware to gain access to sensitive customer data as well. Unfortunately, without proper countermeasures in place, you will not be able to prevent such attacks.
8. Phishing and Baiting
Phishing and baiting fool users into sharing sensitive information with hackers. Phishing attacks can be disguised as fraudulent websites. Regular users are not aware of this. As a result, hackers end up with the important credentials of users.
In general, phishing and baiting require hackers to get information from the users. So, if store owners can take specific measures as to how and what information gets collected from the users, such hacking attempts can be minimized.
9. E-skimming
E-skimming attacks target the checkout or payment pages – gaining sensitive transaction information in real time. These types of attacks originate from brute force attacks, phishing, and other cyber attacks.
The website security needs to be airtight when dealing with threats like skimming. The site needs patch updates to stay on top of skimming attacks.
Then there are DoS (Denial of Service) and DDoS (Distributed Denial of Service) attacks that restrict access to eCommerce sites for a period of time.
Because of these attacks, revenue generation takes a hit – resulting in a loss for the company.
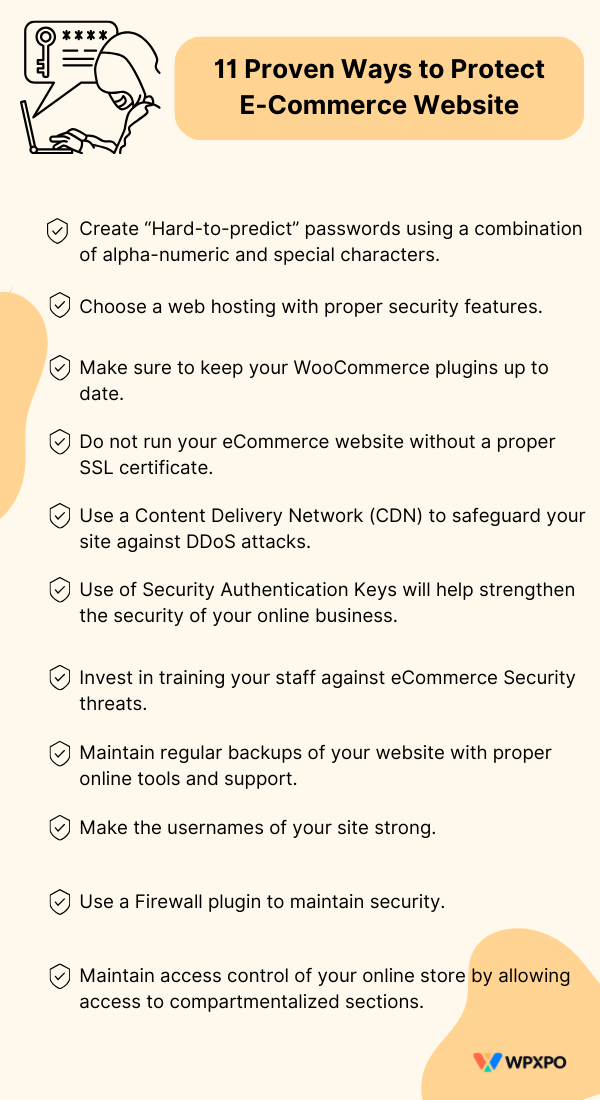
11 Proven Ways to Prevent eCommerce Security Threats [on WordPress]
eCommerce security threats are constantly evolving. This is why it’s super necessary to manage your WooCommerce store – ensuring better security measures.
The following suggestions apply to both customers and WooCommerce store owners. If you take these measures into account, the possibility of security threats will go down significantly.
1. Password Security: Creating Hard-to-Break Passwords
A secure password is the first line of defense against eCommerce security threats. Weak passwords are the entry point for hackers, something you’d want to avoid at all costs.
There are 7 characteristics of weak passwords:
- Using your name as a password
- Using the name of your pets or family members
- Use of the same login code again and again
- Using the same password on multiple sites
- Using common names like phoenix, sunshine, etc.
- Use common password patterns like 123, qwerty, 123456, etc
- Using common words from the dictionary
Hackers exploit these 7 traits to get your personal information and cause harm to your WooCommerce store brand. To be two steps ahead of the hackers, you need to:
- Use passwords that are 12 characters long.
- Do not use any recognizable characters in the password.
- Use special symbols (*, #, ]) within the password.
- Use a combination of upper case, lower case, and numeric characters.
- Do not use dictionary-specific words directly in the password.
These are some of the key things you need to maintain when creating a strong password. According to reports, it can take up to 32,000 years to crack a 12-character password with a combination of upper case, lower case, numeric, and special characters.
And if you feel like you won’t be able to create strong passwords, use a password manager. Password managers like LastPass, Bitwarden, NordPass, etc. are reliable tools for password creation and management.
2. Choose a Proper Hosting for Your WordPress eCommerce Site
Choosing the right hosting for your eCommerce store is crucial to keeping your online identity secure. In general, you need to look for the following features in a hosting that will keep your online store safe from eCommerce security threats:
- Make sure the hosting offers an SSL certificate
- Regular backup service should be available
- DDoS protection offerings should be available
- Site-wide and server-wide firewall deployment
These are the things you should check before moving on to buying a hosting for your WooCommerce store.
A good idea here is to chat with the hosting representatives and check whether or not they are offering the above-mentioned security measures. Also, having a PCI (Payment card industry) compliant payment processor is a huge plus point in this matter.
3. Keep WooCommerce Plugins Up-to-Date
You are using WordPress WooCommerce to maintain your online business, it is crucial that you keep your plugins up to date.
If you do not do so, hackers can deploy measures to hack your website and gain control of your data. WooCommerce plugins offer regular updates, at least that are properly maintained.
If you are using a proper plugin like ProductX for your WooCommerce store or WholesaleX for your B2B storefront, you will be prompted to update them on a weekly basis.
This way, you get the latest features as well as the promise of security.
To update a WordPress plugin, you simply need to:
- Go to your WordPress dashboard
- Click on the “circular icon” at the top of your WordPress dashboard
- It will take you to the update section where you can update themes and plugins
- Select the plugins you want to update and click on update
- After some time, your plugins will be updated.
4. SSL Certificate: Update it for Peace of Mind
SSL (Secure Socket Layer), otherwise known as TLS (Transport Layer Security), is a security protocol for data encryption and server security. It enables HTTPS (Hyper Text Transfer Protocol Secure) for your website, allowing a secure and encrypted connection between a user and your website.
SSL is a common requirement for eCommerce website security in 2023. It is not safe to run an eCommerce website without SSL as you miss out on secure authentication and encryption for your website.
5. Use a Content Delivery Network (CDN)
A CDN is a group of servers set in particular locations that cache site data for users in a location close to those users. As the data is cached in a server close to the user, quick deployment of the data is easier.
A CDN doesn’t just provide adequate security against DDoS attacks but also helps to reduce data redundancy and quick deployment of data to the client’s website. So, using a Content Delivery Network is crucial for both data security and data delivery optimization.
If you wish to maintain a fast and secure eCommerce store, use a CDN!
6. Increase the Use of Security Authentication Keys
A security authentication key works as a secondary authenticator for users. It is like a secure code you enter to access your website or server.
Although these types of services aren’t very scalable, they are very suitable for large eCommerce entities. Also, it only allows authenticated personnel to access the site – making it more secure.
So, this extra layer of security can be very useful if you are an established entity and want to offer access to a handful of people.
But if you are a Small Business Enterprise and want to invest in better eCommerce website security measures, it is best to plan for Security Authentication Keys early on and invest in them.
7. Invest in eSecurity Training for your Staff
eCommerce security threats are changing – attackers are constantly changing their tactics to breach the privacy of users. However, there is certainly a pattern of attacks – there are some obvious markers of cybersecurity attacks.
And you need to train your team so that they can identify these markers. It’s not too late to show them some of the basic things that would help identify security risks and avoid them.
For this reason, it is so important to invest in eSecurity training for your team who help you handle the business.
8. Keep Regular Backups of your WooCommerce Site
It is crucial to keep frequent backups of your WooCommerce store if hackers try and inject malicious code into your site.
WordPress tools like JetPack, and UpdraftPlus are reliable tools for keeping your WordPress website safe and secure.
These are WordPress plugins that can help keep backups of your sites as well as restore your WooCommerce store if you run into any trouble with product updates.
So, make sure to use a proper backup plugin as it will help you with your site’s security as well as help you with A/B testing.
9. Use Strong Usernames
Usernames should be strong as well as the user passwords. In various instances, hackers can get access to your login credentials with the usernames. As such, it is crucial that usernames are strong enough that hackers can’t guess them properly.
Keep the username professional and use special characters in the name to make it more secure.
This initiative will help add an extra layer of security to your WooCommerce site.
10. Use a Firewall Plugin
Your hosting should come with a firewall setup. However, in case there is doubt, you are free to use a WooCommerce firewall plugin as an added layer of security.
AIOS is a good firewall plugin in this case. It has some great features and offers good security for your WooCommerce store.
Also, you can look for other options in the WordPress directory. There are some great fire plugin options you can consider.
11. Control Access to your WordPress WooCommerce Store
You can control access to your WordPress WooCommerce store. There are several types of access you can grant a specific user. Based on the access you assign to the user, specific access to settings will be granted.
So, based on the role you want to set for a user, you can select the access type and save the changes on your WooCommerce dashboard.
Once you do this, the user with the specific access will have access to some features of the site.
There’s another thing you need to keep in mind. And that is Multi-factor authentication (MFA).
MFA implies that a user verifies themselves in multiple ways before access the site. For example, if a user tries to login with their username and password, they need to include a verification code from their mobile device that is sent instantly. There are other approaches as well.
FAQ
You may have a couple of questions about both plugins. We will try and answer them here:
Where do you show upsell and cross-sell products?
In general, you show the upsell products on the product page and cross-sell products on the cart page. ProductX gives you the option to do so.
What is a Product Archive Page?
A product archive page lets you systematically show groups or categories of products. For example, you can create a product archive page with ProductX and show a specific group of products.
Can I build custom banners using ProductX?
Yes, the ProductX banner block allows you to create custom banners of your choice. You can use the in-built settings to create customized banners for your product promotions. You can check the documentation for the banner maker to learn more about the functionalities.
What is the minimum allowed score for reCAPTCHA?
In the WholesaleX, reCAPTCHA settings, you will find a setting called the “Minimum Allowed Score” – here you can set the value between 0.1 to 1.0. The scale measures the interaction between an entity and your website.
If the score is <= 0.3, the entity is likely to be a bot or malicious program. If the score is greater than or equal to 0.7, it is an indication that the interaction is good and the entity is likely a human looking to establish communication with your site.
How to change the store to be a B2C+B2B eCommerce website?
If you go to WholesaleX > Settings > General Settings, you will find the option to change your store from wholesale B2B to a B2C+B2B eCommerce website. All you have to do is select the option and save the changes.
Can I create wholesale pricing for guest users?
Yes, WholesaleX has the ability to set tiered wholesale pricing for guest users. All you have to do is go to Products > All Products from your WordPress dashboard. Select the product to create wholesale prices. Go to Product Data > General > Guest User and add the tiered prices. Make sure you choose “B2B+B2C” in the WholesaleX settings for this to work properly.
Can registered users create subaccounts?
Yes, with the WholesaleX Subaccounts addon, you can enable subaccount creation for desired users. Registered users will be able to create subaccounts from their dashboards.
Can users create custom email templates?
You can create custom email templates with the WholesaleX plugin. Even if you find it lacking in some areas, there is a WholesaleX Email Integration you can try out to get a proper experience.
What is the International Organization for Standardization (ISO)?
The International Organization for Standardization (ISO) makes guided efforts to ensure that an organization maintains their products and services to certain standards. These standards are set by ISO.
The ISO 27001 outlines a set of requirements and practices that allow organizations to maintain their security and confidentiality. An ISO certified business entity maintains the practices and strategies set forth by ISO – meaning they have a set of industry-standard protocols in place.
Will a VPN help secure my eCommerce store?
VPN or Virtual Private Networks create end-to-end encryption keys when a client uses VPN. Now it does introduce some latency, but the end-to-end data connection remains secure, even if some hacker is monitoring data passing through the Internet Exchange Point.
Should I be Worried about a Zero-Day Attack?
A zero-day attack primarily occurs because of software vulnerability. If there is a core issue in the code of the software, attackers release a malware to exploit it – for this reason, it’s called a Zero-day Attack. If you ever face such a vulnerability, unfortunately, there is no way to identify it initially.
What does the GDPR (General Data Protection Regulation) dictate about online security?
GDPR security rules ask companies to secure user data in the safest way possible. The organization is responsible for the data security of its users.
Data breaches in Large Corporations
Here are some examples of data breaches in large corporations. These are all online entities that saw major breaches in their online security:
- Microsoft faced a data breach back in 2021 where 30,000 businesses worldwide were exposed. Hackers exploited 4 separate Zero-day vulnerabilities to execute the attack.
- Because of a sync tool vulnerability, 530 million users of Facebook were exposed in April 2021.
- Another incident occurred in the same year (2021), where 700 million users of LinkedIn were exposed due to an email address vulnerability (possible phishing attack).
- Back in 2014, Home Depot experienced a breach where 56 million credit card details were exposed. Hackers used 3rd party tools execute the attack.
- Adobe experienced an attack in 2013 that revealed 38 million credit card numbers. Reports claim that the attack was likely because of the switch to selling desktop licenses to moving to the cloud.
Keep Your eCommerce Store Safe
Around 91% of E-commerce businesses have had at least one incident regarding eCommerce website security. Also, in 2022, more than 40 billion dollars in damages were reported that originated from cyber attacks.
So, it is super important to pay attention to security for eCommerce. As exhibited above, damage from online attacks can be devastating.
It is our recommendation that you take the 11 recommendations for eCommerce security and try to implement them to the best of your abilities. Although it will not completely eliminate the possibility of an attack, it will help mitigate the damages to a great extent.
Do you think we covered everything? If not, sound off the comments below and show us the breach.
Good luck!